A recent post by Hudson Rock detailed information derived from infostealer logs tied to activity associated with the Trevor Greer persona, you know the one trevorgreer9312@gmail[.]com. That write up provides some context around the data and places it with broader reporting on North Korean IT worker activity. If you haven’t seen it, the article can be found here:
While I had originally planned to do a more comprehensive write up of the logs there’s a more detailed write up already written by Slapdash Safeguards that goes into additional detail about the contents of the logs, beyond what Hudson Rock covered: https://www.sdsg.moe/entry/2025/12/10/233030?_x_tr_sl=ja&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=sc
Before going further it’s worth clarifying that just having the presence of a DPRK linked persona in some infostealer logs does not mean that this is directly connected to the Bybit incident itself. Additionally, much of the data appears to be over a year old. AT this point, it is unclear whether the logs were recently leaked or simply just discovered.

However there are still several details in the logs that have not been discussed so far and are worth highlighting.
Software
One of the more notable findings in the logs is the list of processes running on the machine, including:
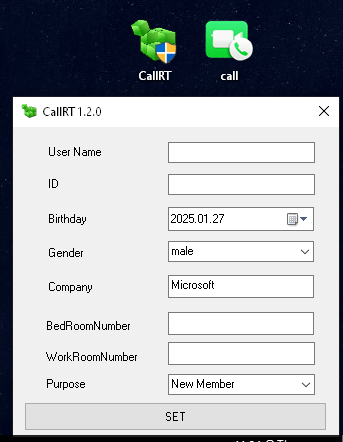
- CallRT.exe
- Call.exe
- Call3.0.exe
These binaries appear to be purpose built utilities associated with DPRK ITW environments. While I’m working on a deeper reverse engineering post at a high level this software appears designed to support application and hiring workflows. Additionally the tool appears to include some keylogging functionality that triggers on specific keywords, as well as providing a way to track where a user is logged in when they first connect with the software.
BlockBounce LLC
The company BlockBounce LLC is also briefly mentioned in the data. The address associated with the company points to an apartment complex in Atlanta:
860 Glenwood Ave SE Apt 409
Atlanta, Georgia 30316
United States

This address is most likely a fake address and should not be treated as definitive evidence of anything on its own. However, the use of residential addresses for shell entities is consistent with patterns seen in other DPRK linked operations.
Additional Identities
In addition to the Trevor Greer persona, the same environment appears to reference other identities, including the name Yeferson Mejia using the email jaider@blockbounce.org. Emails suggest communication with an external service related to recruitment for BlockBounce on an AI-Powered interview platform:

GitHub Account
The username topsdev126 appears in the logs and is also referenced in the Hudson Rock article. That username is associated with a GitHub account, which still exists at the time of writing, though it shows little visible activity:
On its own, the existence of the account does not indicate active use. However, the same username also appears in logs from a commercial proxy provider:
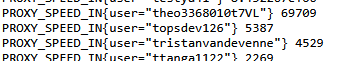
It is difficult to determine from this data alone whether the proxy account is still actively being used or simply remnants of older activity.
While none of these points stand out on their own, combined with other data they may add context to aspects of the data that has not been covered in other write ups.
Discover more from North Korean Internet
Subscribe to get the latest posts sent to your email.
Pingback: All things infostealers. Week 1, 2026 – Kinda Blog by CryptoLek 🍉 🌻