Last year we discovered a North Korean server that was hosting numerous animation files. I wanted to share a more detailed write-up about how we discovered the server, as well as some more details about what we found. You can read the original coverage here: What We Learned Inside a North Korean Internet Server
The Initial Discovery
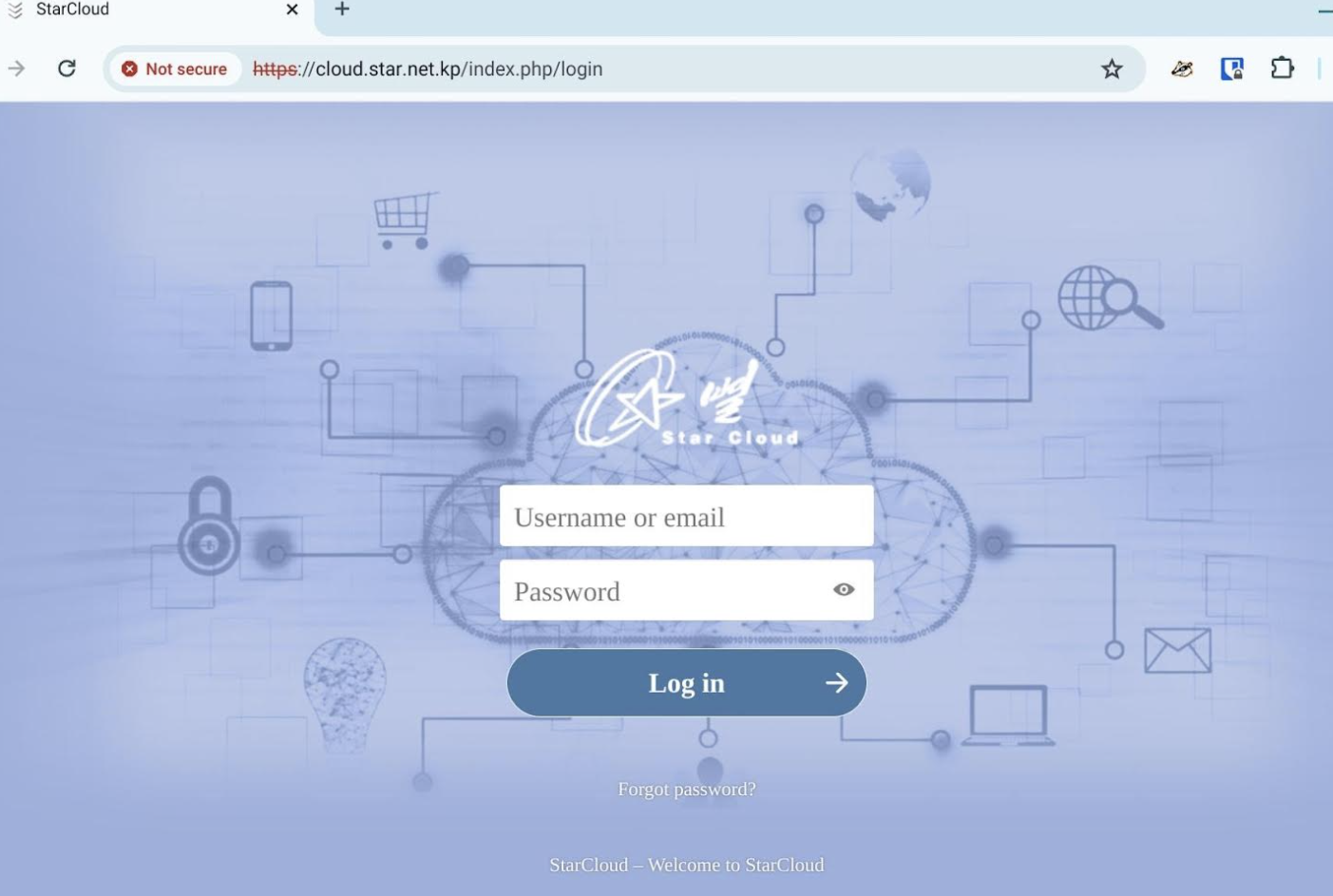
It began at the end of 2023 when I noticed a new DNS record for the domain cloud.star.net.kp which resolved to the IP address 175.45.176.31. At that time I had published a short post about an exposed ownCloud instance running on a North Korean IP: Exposed Nextcloud Instance
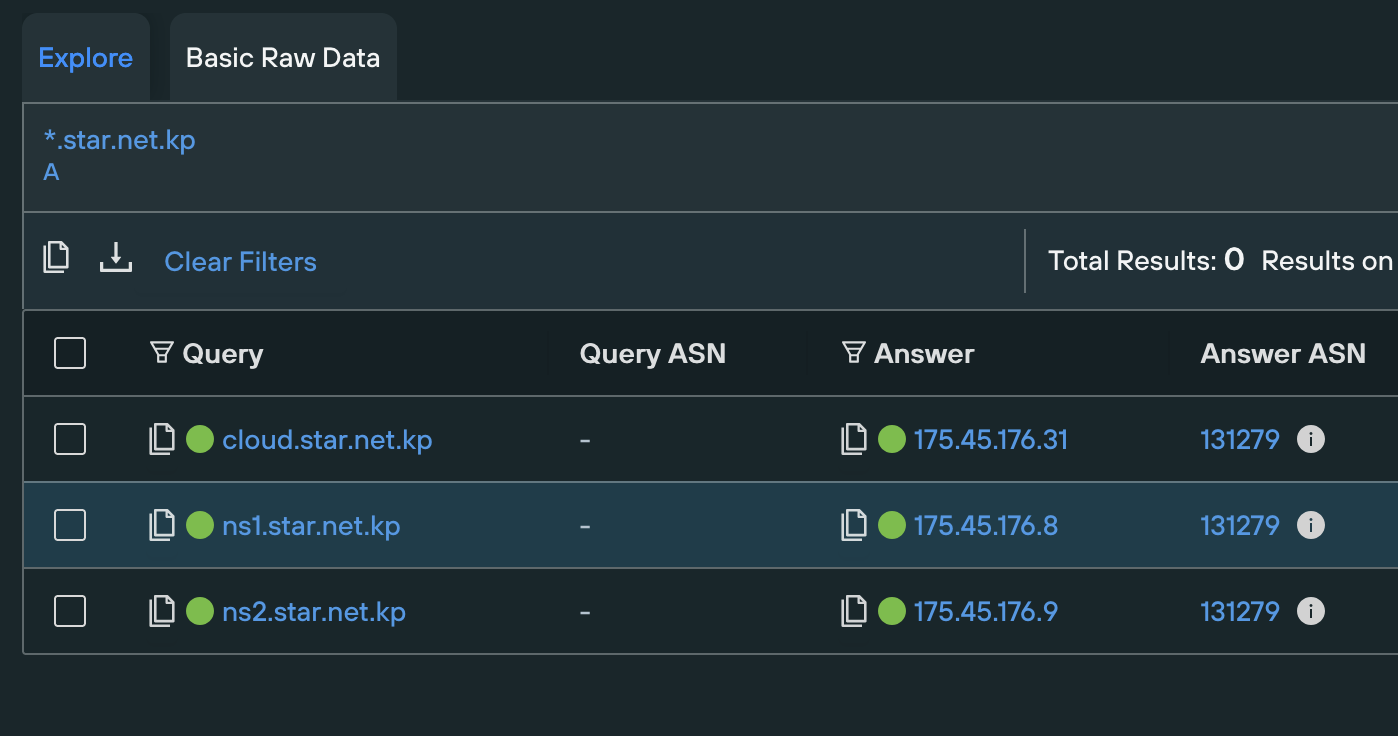
While browsing to the IP directly returned an error page, browsing several common directories revealed several folders that were accidentally exposed, the most notable of which was /data
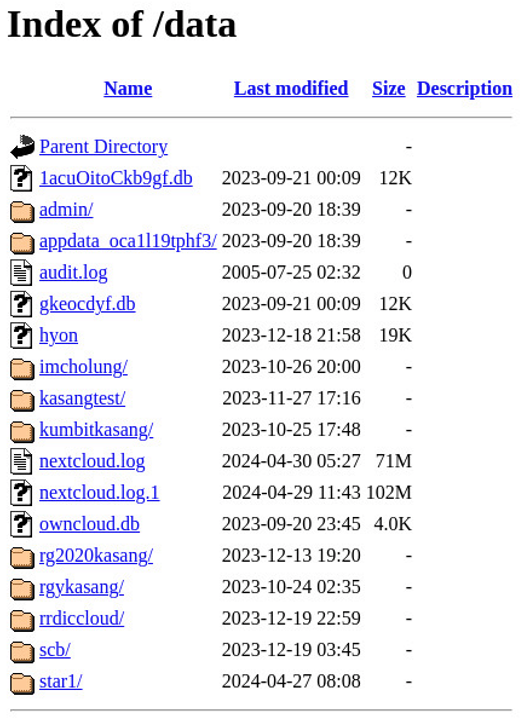
What Was Exposed
The /data directory provided access not only to all of the files for each user but access to the server logs as well. These logs provided additional insights into user activity and where these users were logging in from.
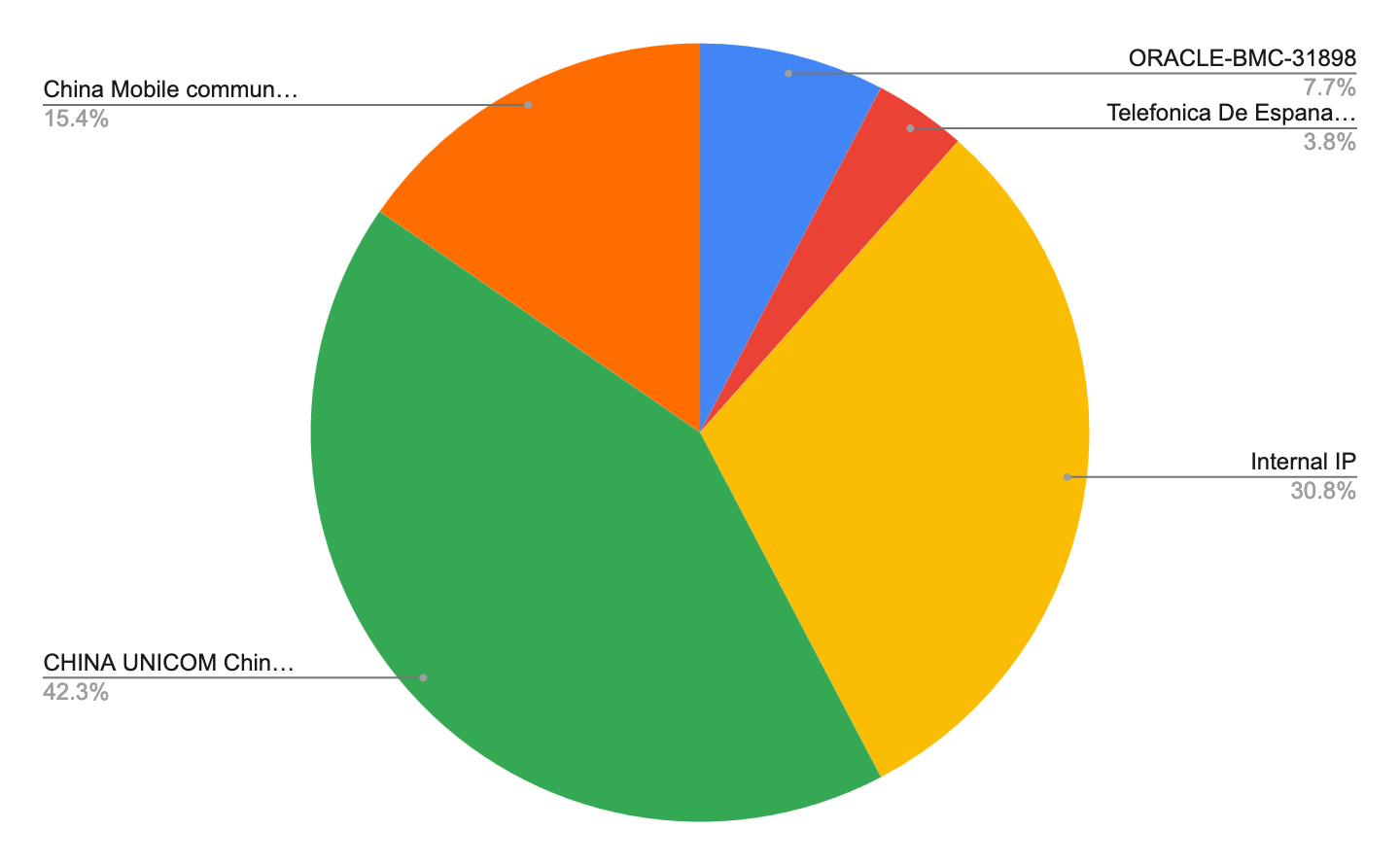
There were several logins that originated from RFC-1918 addresses suggesting users logging in from inside North Korea. In addition to these logins there were several other ASNs that we observed activity from outside of the DPRK
Failed Logins and Suspicious Activity
The logs showed repeated failed login attempts from the following IP blocks
- 104.234.140.0/24
- 85.203.21.0/24
Interestingly the login attempts were using valid usernames and all shared the same user-agent of test, suggesting that this could have been automated attempts but unclear whether they were malicious or benign.
Outside of the users listed in the directory there were also a number of interesting failed logins associated with several usernames:
| 시험 (test) | komogeco |
| asd | 최현성 (Hyunseong Choi) |
| test-m | tkhyp@star-co.net.kp |
| T-81vr-m | jcg0123 |
| pkitc@silibank.net.kp | pyitc |
| pkitc@star-co.net.kp | hyon |
| kitc@star-co.net.kp | imcholung |
| kitc |
VPN Usage
Further analysis of the logs revealed that several of the logins were made with IPs associated with Express VPN as well as VPN Gate which is a free VPN service run by the Univ of Tsukuba in Japan.
Notably when accessing cloud.star.net.kp through VPN Gate we were able to connect to a login page for the ownCloud instance.
How Long Did It Stay Online?
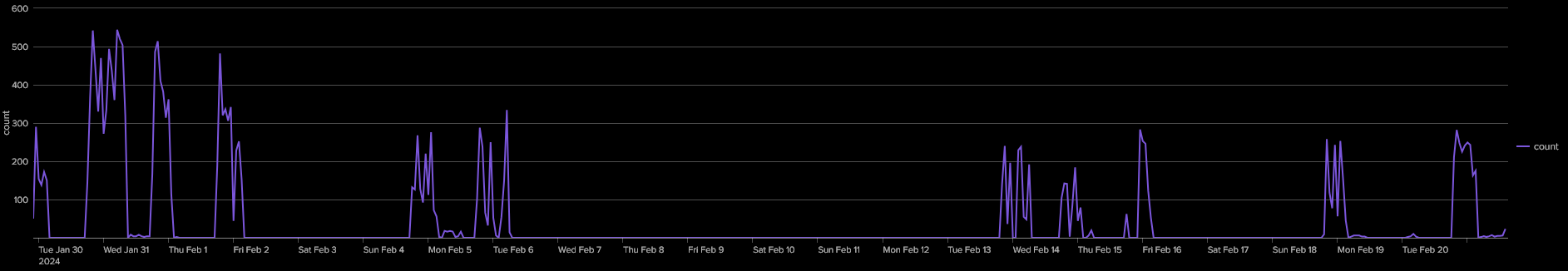
With all of the coverage of the server I had also written a script to track how long it remained online for after all of the articles were published. The original stories were published on April 22nd, but it wasn’t until April 27th that all of the files associated with the user star1 were deleted but the open directory remained exposed. By April 30th some log files were throwing errors when attempting to access but the remaining data was still available. It wasn’t until May 8th around 6 AM GMT that we finally lost all access to the server.
I’ve uploaded a small sample of the files here. The full server contained approximately 250 GB of data. If you’re interested in reviewing the full dataset please reach out. In Part 2, I’ll go into more detail about the contents of the files and some of the more interesting material that we uncovered.
Discover more from North Korean Internet
Subscribe to get the latest posts sent to your email.